IP Whitelisting
IP whitelisting is a security feature often used for limiting and controlling access only to trusted users. For our UAT and Production enviroments we use IP whitelisting to create lists of trusted IP addresses or IP ranges from which your applications can securely access our APIs.
We allow only select IP addresses to access our application over the internet. Hence as a consumer it may be required to whitelist all the ip addresses that the consumer would be consuming the application from. This step is a prerequisite to setup successful connectivity.
Encryption
All communication with our APIs are encrypted. The API to be invoked accepts the request body that is encrypted using encryption algorithm. The encryption key will be provided and will be different for each consumer.
Client Keys
All APIs require Client id and secret that is generated as a part of HTTP Header.
HTTPS and two way SSL
Axis Bank Developer portal provides 2-Way SSL out of the box for a secure and reliable developer and live experience.
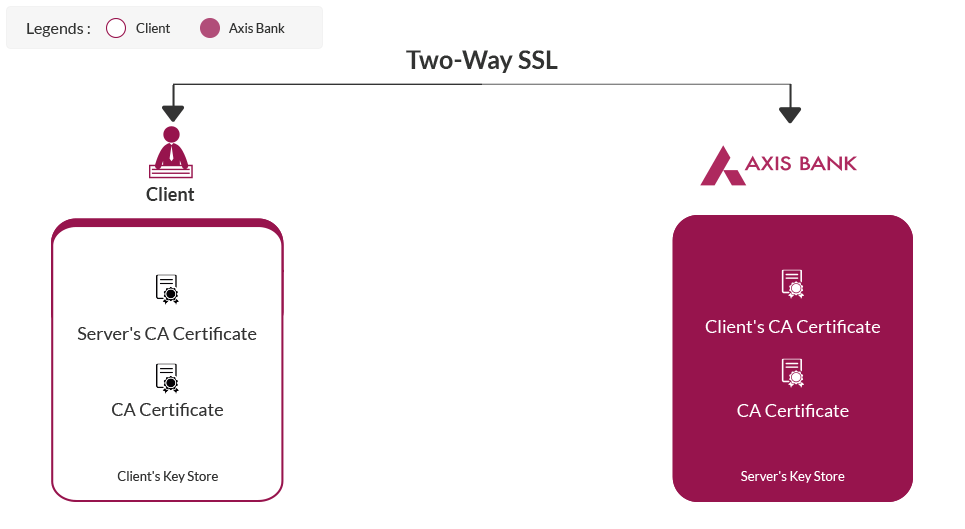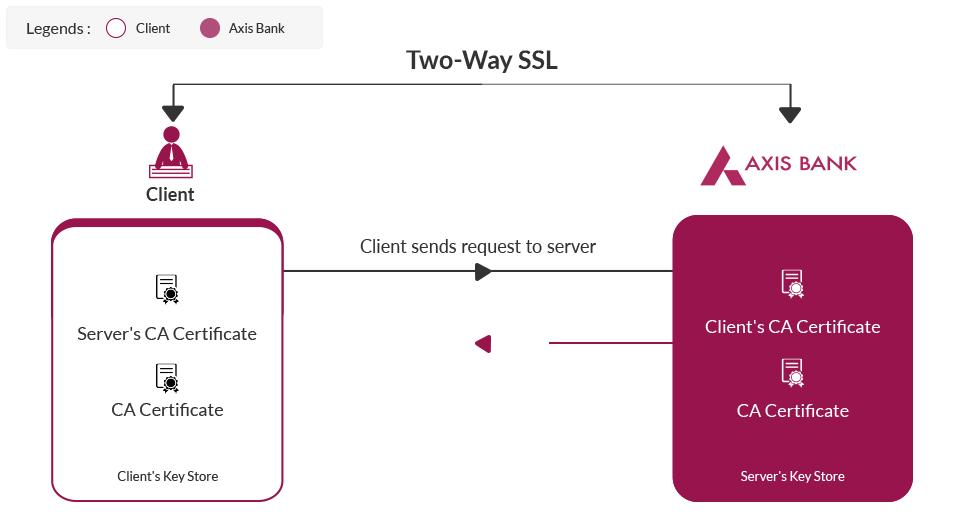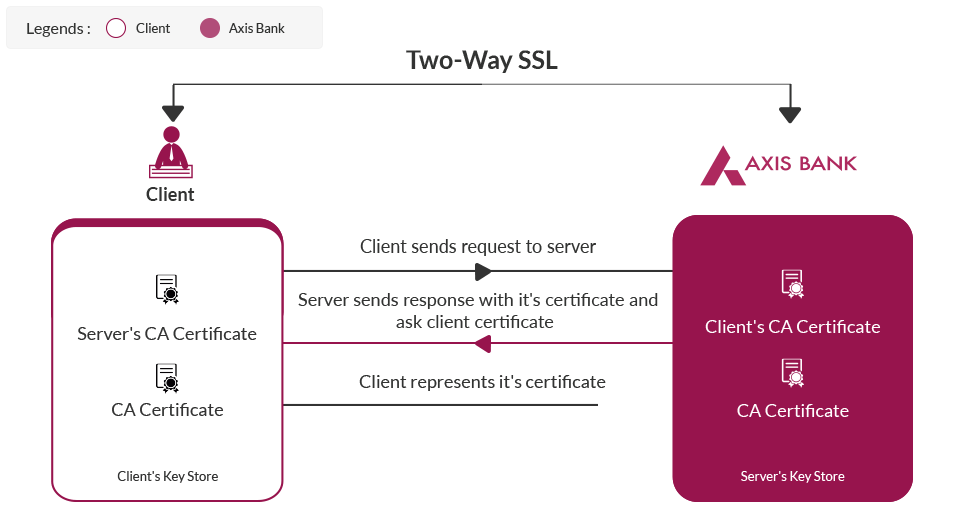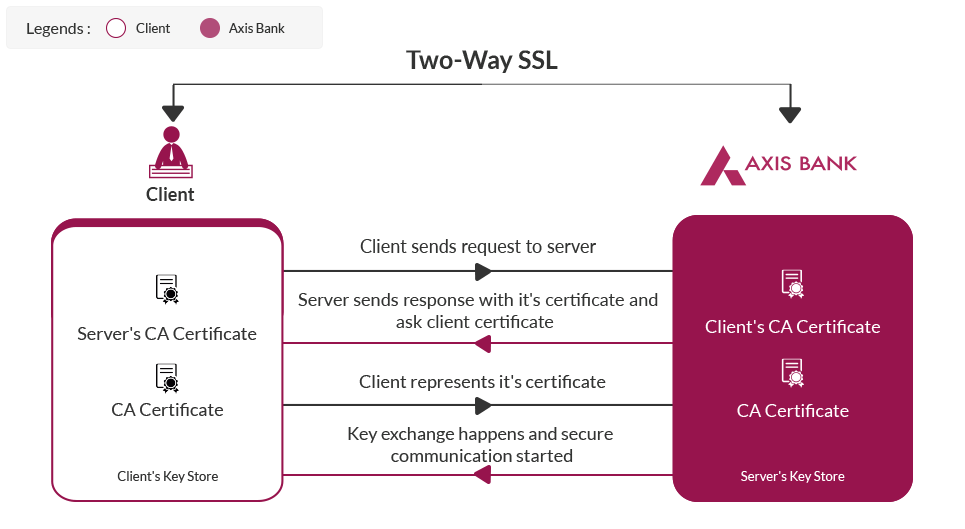
Mutual SSL or two-way SSL refers to both client and serverauthenticating each other at the same time. Which provides higher security compared to 1-way SSL in which only client authenticates the server.
All consumers will be needed to invoke the application over HTTPS protocol. We also have two way SSL established. This means that we would be validating the consumer certificate. Hence it is required that the consumer has a certificate (which may be self signed or a valid certificate from a CA) and the same is shared with us as a pre-requisite
Configuring Two-Way SSL Keystore with OpenSSL
Requirement - openssl library for windows or linux
OpenSSL is an open source implementation of the SSL and TLS protocols. It provides an encryption transport layer on top of the normal communications layer, allowing it to be intertwined with many network applications and services.
1. Step to generate a CSR (to be done by the Consumer).(1-a) Generate a new Private Key
openssl genrsa -aes128 -out > 2048
(1-b) Generate a CSR (Certificate Signing Request)
openssl req -new -key > -out >
When prompted enter a PEM passphrase. Answer the following questions that will be prompted. The answers will be used to generate your .certificate. Answer '.' to leave it blank.
Note: Common Name field must contain a fully qualified domain name. Format should be alias/hostname.domainname.com. This must not contain any wildcard characters for the hostname. Otherwise, use the hostname or IP address set in your Gateway Cluster (for example. 192.16.183.131 or dp1.acme.com).
Optional: Review your certificate using the follwoing command
openssl x509 -text -noout -in >
2. Share the CSR to Axis Bank. Axis Bank will sign the CSR and give you a certificate bundle.
A certificate bundle will consist of the signed certificate and the complete certificate hierarchy (Root and Intermediate).
In this step you will require the key generated in (1)
openssl pkcs12 -export -out > -inkey > -in > -name > -certfile > -certfile >
Configuring Two-Way SSL Keystore with Java Keytool
Keytool is a certificate management utility that is part of the standard Java distribution.
If you use a JKS file as your truststore, follow the instructions below to add the DigiCert Global Root CA certificate to your truststore.
1. Download the DigiCert Global Root CA certificate from https://dl.cacerts.digicert.com/DigiCertGlobalRootCA.crt to your local folder.
2. Backup your truststore JKS file as a safeguard.
3. Then, run the following keytool command to add it your truststore:
keytool -import -alias DigiCertGlobalCA -keystore <Path to JKS (TrustStore) file> -file DigiCertGlobalRootCA.crt
To generate a CSR using keytool:
1. Generate a keystore file that contains public/private key pair (for example: 'keystore.jks'), as shown below, using RSA, a keysize of 2048, and a password. Keytool manages everything through the Java Key Store (JKS).keytool -genkeypair -alias client -keyalg RSA -keysize 2048 -keystore keystore.jks -storepass <password> -keypass <password> -dname "CN=<common name>, OU=<organizational unit>, O=<organization name>, L=<city/locality name>, ST=<state name>, C=<country name>"
Country Name
Two-digit International Standards Organization (ISO) 3166-1 country code. For example: US
State Name
Name of the state or province where the server is located. For example: California
Locality Name
A valid city name. For example: San Francisco
Organization Name
Name of your organization. For example: Bank of USA
Organization Unit Name
Name of your division within your organization. For example: Debit Card Processing Unit
Common Name
This field must be a fully qualified domain name. Format should be alias/hostname.domainname.com. This cannot have wildcard characters for hostname. For example: apiportal.axisbank.com
Note: For all fields, only following ACSII characters are allowed.
- Space Character
- Upper case A to Z
- Lower case a to z
- Digits 0 to 9
- Dash (-)
keytool -certreq -alias client -keystore keystore.jks -storepass <password> -keypass <password> -file cert.csr
You now have the Java Key Store file (which contains your private key) and the CSR file.
Certificate (root CA) and the certificate (client cert) to a local folder. You should see both AXISCA.pem and cert.pem in your local folder.
3. Update Java Key Store with Root Certificate and Client Certificate using Java Keytool.
To invoke an API using Two-Way SSL, you must have a client certificate and your root CA in your keystore, since your Java SSL library only accepts one input for all certificates – the keystore. Therefore, you will need to add the certificates downloaded from Axis Developer Portal to the keystore (for example: keystore.jks) that you generated while creating the CSR.
To add a project-specific certificate to the keystore:
1. Add the Axis Developer Portal CA Root Public Certificate to the keystore:keytool -import -alias ejbca -keystore keystore.jks -file AXISCA-Sandbox.pem -storepass <password>
Note: Replace the above with the actual password that was used while creating the keystore.jks.
Click yes when prompted to trust the certificate option.
2. Add the project specific certificate to the keystore:
keytool -import -alias client -keystore keystore.jks -file cert.pem -storepass <password>
The resulting file, called keystore.jks will contain your private key, your client certificate and your Axis Developer Portal CA root certificate.